Yesterday, I posted about attending a Domino Jam for the first time in six years and my feelings on how HCL has turned the product around. Today I want to touch on the security aspect discussed at the Jam and add my thoughts to the mix.
Secure by Design
Immediately following the roadmap presentation, the jam looked at Domino's legacy and where it is today. One of the key takeaways from this was a discussion of the incredible security in Domino. We have seen this in our organization but it was nice to hear HCL and other organizations (via quotes and stories) saying the same thing.
There are many good reasons for the high security score but two of the best are
- Multi-layered security from the very beginning of the product.
- Domino being "on-prem" rather than web hosted.
There were a couple of interesting stories and observations, including one about a penetration test on one of the new tools (Volt) where the auditors talked about the many layers of security in the Domino back-end and the fact that it was simply not worth a hacker's time to get through all of them when there are much easier targets.
There was talk of the many standards that Domino currently supports and new standards being supported in the next upgrade (DKIM and others). HCL claims that Domino is still unbeaten in internal mail security. It's a bold statement but it has some merit, particularly when the on-prem systems support tough encryption and could be run in a completely firewalled internal environment.
One of the participants remarked to me during a break that it was interesting that the organizations that hold onto Domino tended to be the types of organizations to whom security is considered a high priority. From what I've seen, it's true. If you're willing to move off domino, you also have to accept that your security will take a hit.
Maintaining Security
Inevitably, there was a question about why anyone should upgrade if the security was so good. I sighed inwardly at that one. If you're still running Domino 9, then you're running a system that was designed for Windows Server 2012 (or Windows PC 8). Those operating systems had holes in them like Swiss cheese and it would be dangerous to run those platforms today.
It's not just windows that has been upgraded and patched though. Domino has had its fair share of fixes and new security features since release 9. This includes
- Mitigations for BEAST, POODLE and GOLDENDOODLE SSL and TLS vulnerabilities
- Retirement of older protocols (and introduction of new ones)
- Mitigation for Cross Site Scripting (at R12).
If you're running anything below R12.0.1 plus fixes, you're not doing your best to deal with your security issues. That's why it's so important to keep up your maintenance with HCL current.
Testing Security
It's not enough to simply maintain security. You also need to keep testing for vulnerabilities. There's a bulletin on the HCL site which you can subscribe to that will send you notices of vulnerabilities when they are found. It's worth subscribing to keep "in the know".
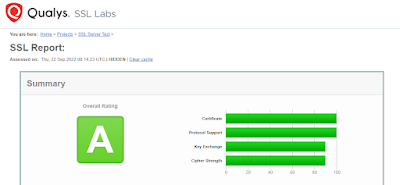
If your domino server is hosting portals, web or extranet pages, it needs to be running SSL throughout but that's not enough. You need to be checking it regularly (at least six-monthly) against the excellent SSL tester from Qualys. Anything less than an A rating is not good enough and needs to be patched. If you're struggling with this, ask HCL for advice on lifting your rating.
Then there are audits and penetration tests. We run these at least annually but we also run them whenever we deploy new systems (we build them into the development costs). You should be reading the output of your penetration tests and acting on the advice you have been given.
You also need to consider the following;
- Domino Versions and fix packs - also your client versions.
- Protocols in use - did you know that you can (and should) disable old protocols.
- Notes.ini - this can have outdated entries that should be removed. You can also improve security with a few choice lines in this file.
- Site documents - Are all your sites still in use? Are all the settings there still relevant?
- Encryption levels within IDs
Comments